
Cyber Security Services in Hampshire
Cyber Security Managed Services with a Zero Trust approach
Under One Cloud supports a comprehensive Zero Trust approach to technology. Zero Trust is a modern security strategy built on the principle of never trust, always verify, and it forms the foundation of our cyber security services across the UK.
As a Hampshire-based provider delivering services on a national scale, we place cyber security at the heart of every business IT decision. Our Zero Trust mindset simplifies the integration of new technologies and ensures your organisation benefits from robust, future-ready protection.
From the outset, we committed to delivering IT and cyber security managed services without compromise. Every service plan includes a full stack of enterprise-grade IT and security software to establish a mature and secure baseline for your business.
All customer deployments include:
- Microsoft 365 Business Premium
- Full Microsoft 365 Backup Solution
- Security Suite and Cyber Security Training
- Remote Monitoring
- Policy Management
- DNS Filtering
- Helpdesk Support
- Email Signature Management
(Partner names intentionally withheld)
Our service stack is designed to evolve, with new tools and enhancements added each year. With Under One Cloud, your IT and cyber security posture will continuously improve — we’re fully invested in supporting our customers’ long-term success and defending you against malware attacks.
Contact us to discuss your current cyber security set up.
Zero Trust as a Way of Thinking to Protect Against Cyber Attacks
Full Stack, no compromises approach to IT cyber security. Its the new modern way to think about your IT defence and protection.

How Our Cyber Security Services Can Help You
Defence and Protection
Our Defence and Protection services deliver a strong first line of security for your organisation. We combine industry-leading tools with our Zero Trust approach to safeguard your systems, data, and users from emerging cyber threats. As a Hampshire-based cyber security provider operating nationwide, we ensure your business is protected with continuous monitoring, advanced threat detection, and secure policy enforcement—giving you confidence that your digital environment is always resilient against malware attacks.
Managed Backup and Disaster Recovery
Data loss can bring any business to a halt, which is why our managed backup and disaster recovery solutions are built for speed, reliability, and complete business continuity. We implement secure, automated backups alongside rapid disaster recovery options to minimise downtime and financial risk. Your data is protected, encrypted, and easily recoverable—forming a crucial part of our cyber security managed services offering.
Proactive Threat Prevention
Our Proactive Threat Prevention service focuses on stopping attacks before they reach your systems. From real-time monitoring and intelligent DNS filtering to behavioural analytics and ongoing policy management, we work around the clock to identify and block threats early. This proactive approach strengthens your overall cyber security posture and ensures your business remains one step ahead of cyber criminals.
Cloud Security
With more organisations relying on cloud platforms than ever, secure cloud environments are essential. Our Cloud Security service protects your Microsoft 365, cloud infrastructure, and data from unauthorised access and misuse. Using Zero Trust principles and advanced cloud monitoring, we ensure your cloud environment remains compliant, controlled, and fully protected—no matter where your team works.
Microsoft 365 Cyber Security and Conditional Access
Conditional Access Policies within Microsoft 365 enable us to control and secure access to your business resources based on specific conditions. For example, we can create policies that allow only a designated group of users to sign in from approved macOS devices, and ensure those devices meet the required compliance standards before access is granted.
To maintain a consistent and secure environment, we deploy a standardised set of Conditional Access Policies across all clients. These typically include:
- Location-based access restrictions
- Access limited to managed devices and approved applications
- Enforced Multi-Factor Authentication (MFA)
- Requirements for secure, approved apps only
We also use a service called Inforcer to distribute our policies, track changes, and maintain full compliance across every customer environment. This ensures your organisation benefits from robust, centrally managed, and continuously monitored security controls.
Contact Us To Discuss Microsoft 365 Cyber Security Options

Our Approach to New Technology
The Zero Trust Approach allows us to efficiently assess new technologies by ranking against specific criteria.
Business need, benefits, drawbacks, ROI and security are all important considerations.
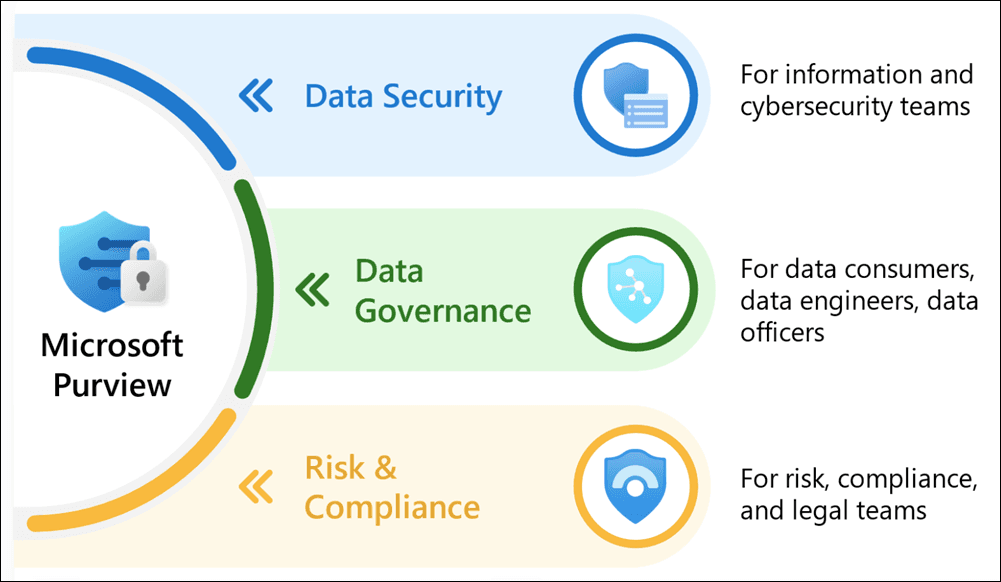
Implementing new technology doesn't need to be daunting. Due to the way we standardise our services, we have the time to investigate, secure and deploy new technologies with the help of in-built Microsoft 365 Systems such as Microsoft Purview.
Expert IT and Cyber Security Services
Managed IT Support
Managed Cloud
Microsoft 365 Managed Services
New Technology Exploration and Consultancy
We can leverage our direct Microsoft credits and Partnerships to help explore new technolgies and secure them with the help of Microsoft Purview for 365
Frequently Asked Questions
Start defending your business against cyber threats today!
